Cyber Security Tabletop Exercise
What is Cybersecurity Tabletop Exercises?
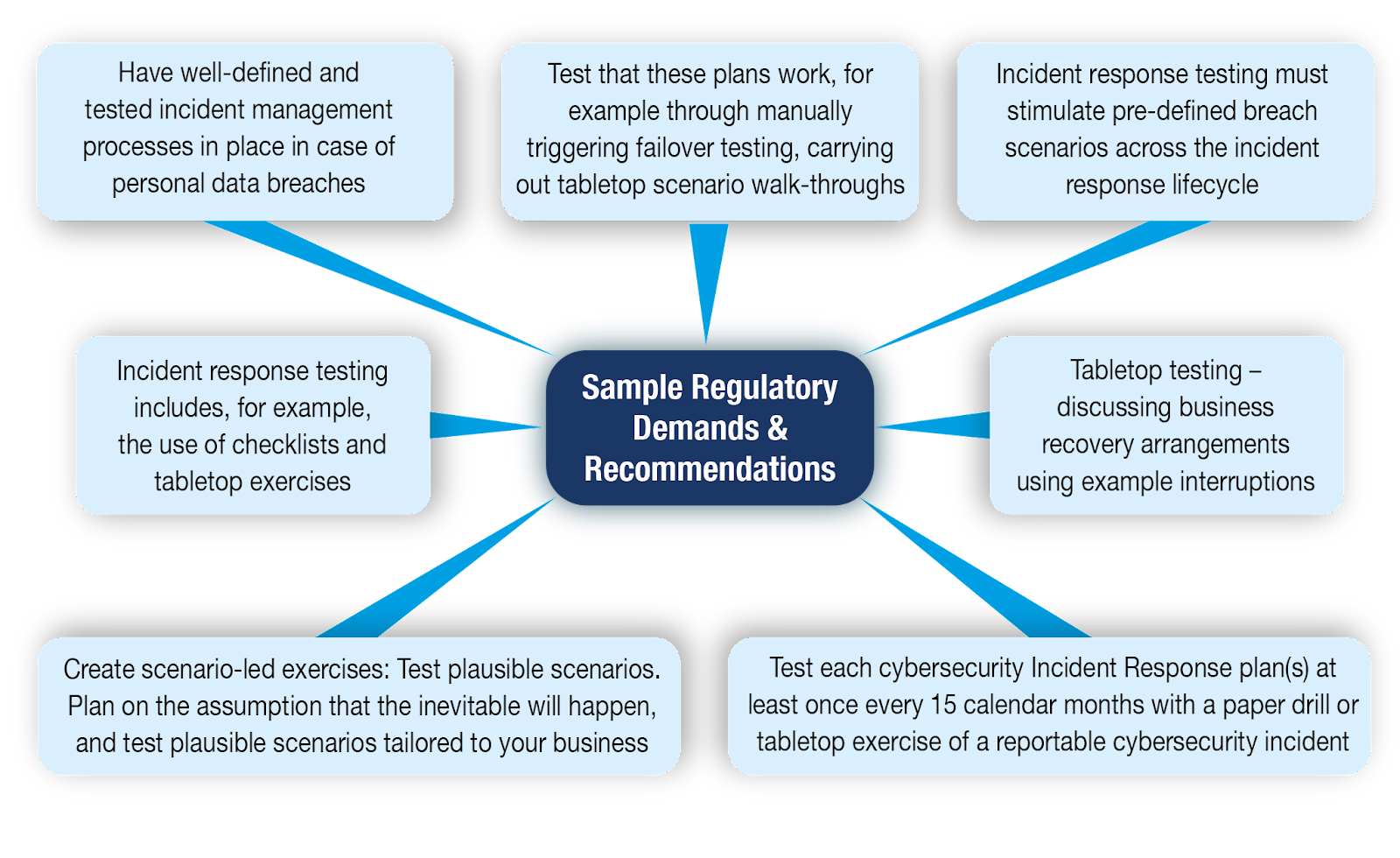
Key Elements of Cybersecurity Tabletop Exercises:
1. Scenario Development: We would collaborate to create realistic scenarios that mimic potential cyber threats relevant to our organization. These scenarios could include ransomware attacks, data breaches, or system compromises, allowing us to explore vulnerabilities and response strategies specific to our environment.
2. Participant Engagement: We would invite participants from various departments and levels of the organization to participate in the tabletop exercise. This diverse representation ensures a comprehensive evaluation of our response plans and fosters collaboration among stakeholders.
3. Simulation Execution: During the exercise, facilitators would present the scenario, prompting participants to engage in discussions, decision-making processes, and response actions. By simulating real-world incidents, we can test our knowledge, communication channels, and incident response protocols in a risk-free environment.
4. Evaluation and Feedback: Following the tabletop exercise, we would assess our performance and gather feedback from participants. This evaluation process helps us identify strengths, weaknesses, and areas for improvement in our response capabilities, informing future training and preparedness efforts.
Value of Cybersecurity Tabletop Exercises:
Risk Identification and Mitigation:
Through tailored scenarios, we can identify vulnerabilities in your systems and processes that could be exploited by ransomware attacks. By proactively identifying these weaknesses, we can implement targeted risk mitigation strategies to prevent infections and minimize the impact of potential attacks.
Enhanced Preparedness:
By simulating ransomware scenarios, we can familiarize your team with the specific steps required to detect, contain, and eradicate infections. This includes understanding how to isolate infected systems, restore data from backups, and negotiate with attackers if necessary, ensuring a swift and effective response.
Stakeholder Collaboration:
Involving stakeholders from across your organization fosters collaboration and strengthens relationships, enabling smoother coordination and communication during incidents. By ensuring everyone understands their role and responsibilities, we can streamline your response efforts and minimize disruptions.
Continuous Improvement:
Insights gained from tabletop exercises enable continuous improvement of your cybersecurity strategies and response plans. By updating procedures based on lessons learned, investing in additional security controls, and providing targeted training, we can better protect your system from ransomware threats.
Value of Cybersecurity Tabletop Exercises:
Risk Identification and Mitigation:
Through tailored scenarios, we can identify vulnerabilities in your systems and processes that could be exploited by ransomware attacks. By proactively identifying these weaknesses, we can implement targeted risk mitigation strategies to prevent infections and minimize the impact of potential attacks.
Enhanced Preparedness:
By simulating ransomware scenarios, we can familiarize your team with the specific steps required to detect, contain, and eradicate infections. This includes understanding how to isolate infected systems, restore data from backups, and negotiate with attackers if necessary, ensuring a swift and effective response.
Stakeholder Collaboration:
Involving stakeholders from across your organization fosters collaboration and strengthens relationships, enabling smoother coordination and communication during incidents. By ensuring everyone understands their role and responsibilities, we can streamline your response efforts and minimize disruptions.
Continuous Improvement:
Insights gained from tabletop exercises enable continuous improvement of your cybersecurity strategies and response plans. By updating procedures based on lessons learned, investing in additional security controls, and providing targeted training, we can better protect your system from ransomware threats.
- In conclusion, SOC 2 reporting service is a valuable investment for organizations seeking to demonstrate their commitment to security, compliance, and risk management. By partnering with experienced professionals, organizations can achieve SOC 2 compliance, enhance trust and credibility with customers and stakeholders, and gain a competitive advantage in the marketplace.

